|
The GAO analyzed six randomly selected Department of Defense (DOD) programmes based on fiscal year 2023 budget size and grouped the investments into three groups — greater than $100 million, between $100 million and $10 million, and between $10 million and $1 million, with key findings that vendors:
Not a good story, although no doubt a common one that, given CIO's and CTO's relentless push to the cloud in recent times, (fully endorsed by doe-eyed executive committees and boards clambering to chat that 'yes, we're doing that too') are unlikely to get air time in that respect - just glowing reports of progress and ever increasing (perhaps slowly) 'number of migrated applications' statistics. Now we're not saying there is no place for the cloud - there is - but per the recommendations of the GAO from this report, it needs to be formulated through guidance and plans that fully address identifying, analyzing, and mitigating the impacts of restrictive software licensing practices on cloud computing efforts. And therein is the problem. Many CIO's and CTO's would rather rely on vendors or consultants recommendations rather than their own in-house expertise across IT, SAM and procurement teams who know in detail what - and where - costs and impacts are likely to arise. So if nothing else, perhaps try to use the GAO's Examples of Reported Restrictive Software License Practices table below as a minimum checklist of what to consider with your next cloud migration programme - it might bring some future issues to light and maybe even save just a little grief! 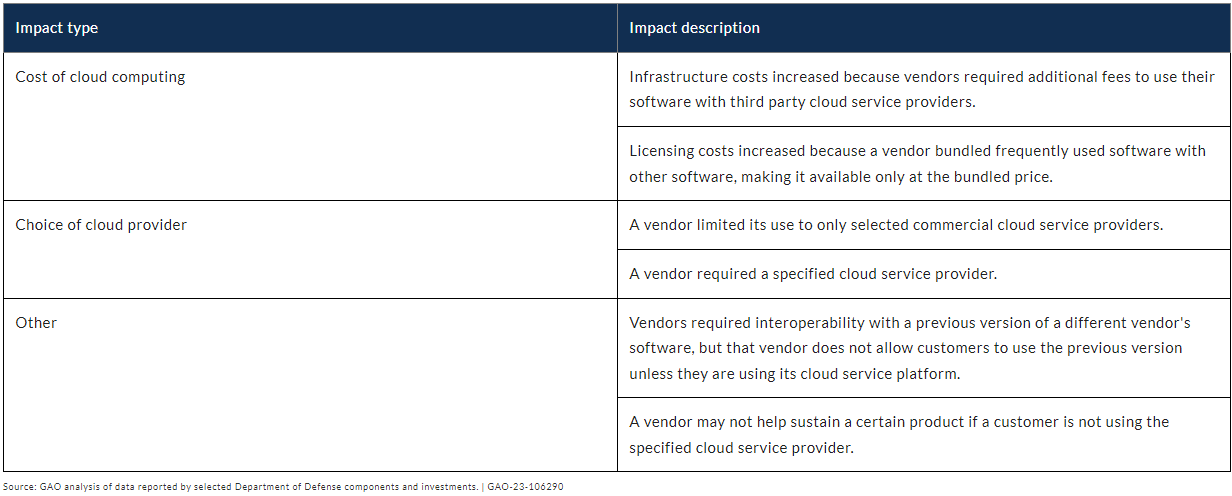
0 Comments
... maybe not.
While companies continue to pursue their relentless campaign of 'moving to the cloud' could they be overlooking their on-premise software position? (similarly, if you're not tracking and aligning your cloud consumption accurately you might be overpaying just the same, but lets just look into on-premise). At a recent (2022) webinar broadcast a former Oracle license management services (LMS) manager, Adi Ahuja, said that Oracle's audit has become "a sales enablement tool." Although Oracle states that their LMS "operates independently from any ongoing commercial discussions. Our services are delivered by a global team of highly experienced and knowledgeable consultants who collectively offer unrivaled knowledge on all aspects of Oracle's licensing policy." in practice there was a close relationship between sales and licence audits, Ahuja said. No surprise to anyone who has been subject to such an audit. But lets not single out Oracle - all of the majors undoubtedly co-ordinate an audit internally - bringing in the product team, finance, sales, and of course, the account team. Ok ... we get that, but how does the software baseline assist us in establishing what's really going on?Take the often cited audit line of 'we found a few things, but you'll just need to top up those products'. Easy enough - you buy the products in the renewal at your entitled price and all is good. What you're not potentially seeing though is the compliance cost as a result of those findings that has been built-in to your renewal fees. Compliance cost? The renewal fees look fine - what are we referring to? Well simply, you might have got a better price overall had you been able to breakdown where those costs came from, and that means having a costed baseline (ie. line-item level) that you can apply all of the adjustors to (inflation, price increases etc) and determine whether any 'additional' costs have covertly come in to play - aka, a compliance cost. Only then can you challenge the vendors assertion that 'you'll just need to top up those products' given what the baseline will tell you is how much backdating has been applied, whether the top-up was in fact at entitled price, and ultimately whether the overall renewal fee has been indexed reasonably at all. Consider the room your vendor has to move when you're faced with a multi-million dollar renewal - there are numerous places to 'hide' revenue pulls, and that doesn't change at lower levels, it just scales down. Establishing and maintaining a baseline can be something companies flinch at - they see it as just not worth the effort - by default then delegating this to their vendors, aka granting free rein to manipulate pricing as they see fit. So while it might take a concerted project (or how about an actual SAM practice!) to get going once established - and maintained in a purpose built system such as ComplianceWare - the overheads are much reduced and the benefits more easily returned. Further, it sends a convincing message to your vendors that you actively manage and are across your software landscape and commercial position, which makes them much more wary of any attempts to hoodwink you with a 'great renewal offer that puts any compliance issues to bed'!
Tucked away (as usual) outside the summary of updates is clause 4.1 - License Verification and to a lesser extent 10.2 - Client's Reporting Responsibilities (applicable to sub-capacity licensing), which compound compliance and reporting obligations - lets take a look. Firstly, clause 4.1.(a) states the "Client will, for all Programs at all Sites and for all environments, create, retain, and each year provide to IBM upon request with 30 days' advance notice: i) a report of deployed Programs, in a format requested by IBM, using records, system tools output, and other system information; and ii) supporting documentation (collectively, Deployment Data)". Unlike version 10 of the PA Agreement (November 2017) which contained a much more lenient requirement that "Client agrees to create, retain, and provide to IBM and its auditors accurate written records, system tool outputs, and other system information" which would occur simply "on reasonable notice" rather than a regular, annual basis. Adding to this, where running under sub-capacity licensing as before you are then required to "properly install, run, and maintain the most current version of the applicable license reporting tool within 90 days of Client's first deployment and produce a report. Unless IBM approves a different reporting tool, the Client agrees to the following tools.
Ok, no real change there and easy enough right? Well yes, you're still required to run and keep reports at minimum quarterly and retain for a two year rolling period - and remember to have an individual(s) who is assigned the "authority to manage and promptly resolve questions on reports or inconsistencies between report contents, license entitlement, and the applicable license reporting tool". Better check that's been added to the appropriate JD's along the way. The new clause 10.2.(e), is somewhat favorable to the client in that it provides an avenue to address (with IBMs consent) deviations from the sub-capacity model, which in most cases would probably result from operating systems becoming non-eligible over time. What we (and others) have always attested to though is being solely reliant on one reporting tool, like ILMT, can prove very problematic in that where improperly configured you could easily be over-reporting and paying much more than you should - having an independent product (like ComplianceWare) is often the best - or only - way to reconcile outputs and ensure accuracy. so ... when does all this start?Well, basically now:
Internal Audit Report highlights flaws in NASA's SAM Practices that many organizations will relate to.The OIG summary of their SAM audit says it all:
... with all of the above quantified in cost terms as:We estimate the Agency could have saved approximately $35 million ($20 million in fines and overpayments and $15 million in unused licenses) and moving forward could save $4 million over the next 3 years by implementing an enterprise-wide Software Asset Management program. All very compelling to implement improvements and progress NASA’s Software Asset Management from “basic” — the lowest of the four rating options in the Software Asset Management Maturity and Optimization Model developed by Microsoft — through the scale as per tiers and representations below:
The report is an insightful read for all SAM practitioners - and responsible management and executives - with clear language and succinct descriptions of the scope and challenges in the field of software asset management, and a pragmatic approach to the creation of an effective SAM Practice that applies to any size organization with a notable software inventory, not just those on the NASA scale. So, to the findings ...It was recommended that the Chief Information Officer: (1) establish enterprise-wide (institutional and mission) Software Asset Management policy and procedures; (2) implement a single Software Asset Management tool across the Agency; (3) align the Agency Software Manager position to report to the Agency Chief Information Officer; (4) establish formal legal representation and guidance for vendor software audits; (5) establish a software license awareness training ‘short course’ focusing on approvals, compliance, and other issues a general user might encounter; (6) implement a centralized repository for NASA’s internally developed software applications; and (7) develop an Agency-wide process for limiting privileged access to computer resources in accordance with the concept of least privilege. Additionally, to strengthen the financial aspects of NASA’s Software Asset Management it was recommended that the Chief Financial Officer: 8) implement a “penalty spend” classification in SAP to track license infractions and true-up payouts and 9) centralize software spending insights to include purchase cards. Nothing fresh there, just the usual (and often unheeded) advice.Unisphere Research, a division of Information Today, Inc., surveyed the readership of its Database Trends and Applications publication, which consisted of database managers, developers, CIOs, and IT directors. The survey, which sought views and experiences with software licensing and audits, was conducted in partnership with LicenseFortress gathering a total of 283 usable responses of which 155, or 69% of survey respondents, reported having been audited within the past three years, and 79% reported having been subject to a software audit within past five years. And the key findings? - the same fundamental approach and issues persist:
Lets take a closer look ...Interestingly, with all the hype and suggested benefits and advantages of moving to the cloud, close to 80% report that it has not changed their software compliance issues, or, in the case of 38% of respondents, it has increased compliance concerns. Only about one-fifth - 21% - say cloud has reduced their compliance issues. And even with close to half - 46% - reporting significant amounts of applications and data in the cloud (defined as greater than 25%), more than half of enterprises reported being audited by one or more software vendors! Similarly, audits themselves haven't changed much at all with 60% of respondents reporting their software audits lasting up to two months, 30% reporting audits lasting between three to six months, and 10% had audits extending more than six months into a year and beyond. The length of audits had 41% of smaller companies wrapping` up audits within a month, while half say the process lasted beyond three months, and 64% incurring additional charges for noncompliance. A substantial portion, 35%, had to pay $100,000 or more to achieve compliance with the vendor, while 10% saw $1 million or more in fees. So, in summary :Unsurprisingly, given the outcomes haven't essentially changed, the underlying good practice principles have also not changed - Software Asset Management is seen as critical to mitigating the impact of software audits by a significant share of respondents. Close to half, 44%, see SAM as essential to reducing the costs of their software, which is impacted by vendor audits. Another 41% cite the importance of SAM in avoiding compliance issues, with the leading choice being an internal software asset management/IT asset management (SAM/ITAM) team supported by SAM specific third-party tools. Disappointingly, it seems many respondents still remain reliant on vendor resources to support their audit. For some of the key underlying data click through the graphs below ...If you rely on IBM Sub-Capacity licensing its a good idea to check you are meeting the compliance requirements on a regular basis ...You no doubt recall that IBM divested the BigFix portfolio of products to HCL in 2019, however maintained ILMT (which remains based on BigFix Inventory), as their free license measurement tool that can be used to meet the reporting and validation requirements under the sub-capacity rules. There is no escaping the sub-capacity rules - as IBM states: "the use of ILMT is recommended for Full Capacity PVU environments, and is mandatory for use with PVU sub-capacity licensing". There are some exceptions to this requirement, essentially though, its only where you measure everything at Full Capacity. So a quick recap of the base requirements for sub-capacity licensing:
The other validated tools? Only Flexera One with IBM Observability IT Asset Management and Flexera One IT Asset Management at this time. Now there are some 'tricks and traps' in running ILMT that we reported on back in 2020 (refer blog here), so make sure you're aware of and managing those gotcha's, and then you'll need to ensure that your IT team is across the eligible technology requirements - most notably - 'Eligible Operating Systems'. These are regularly updated - with only 180 days notice of any withdrawal - so you might find yourselves exposed to the untenable position of being denied sub-capacity licensing based on the OS you're running - as an example, the earliest eligible version of Windows Server is now 2012 ! It can be very easy to lose sight of these changing conditions, and doing so at best can be very problematic, at worst very expensive, so make sure keeping current is diarized in your (and the relevant IT teams) calendars. Further, ILMT itself will need roles assigned to maintaining versions and your software catalogue, and also meeting the quarterly reporting requirements. Keep in mind ILMT retains historic data, so any late changes might well be contested under audit, so better to keep on top of your situation on an ongoing basis. ... all good reasons to perform a timely health-check across your IBM sub-capacity licensing.Hats Off to IBM for it's new dedicated Licensing and Compliance site.Launched on the 17th February the site is a comprehensive, easily navigated resource for both SAM beginners and experienced personnel alike. Quoting Wes Mantle from the Licensing and Software Sales division: "We hope our Licensing & Compliance website will be a go-to resource for IT executives and SAM/license managers, providing clear guidance for measuring deployment effectiveness and navigating software verification process in an efficient, fair and timely manner."The 'Licensing' section offers a good starting point with links to related subjects and material, and also provides particularly good graphical representations of IBM's many agreement structures along with key terms and clauses, while the 'Measurement' section covers the array of metrics and topics across on-premise, cloud and mainframe platforms. If short on time, on everyone's list should be a read and review of the new licensing Guides that include:
The guides have been re-written in a much more readable and informative style covering all fundamental licensing subjects including the often misunderstood virtualization, backup and recovery, and non-production environment rules and obligations. Of course the site wouldn't be complete without covering IBM's Verification approach, which includes audits, self-declarations and the IASP program. Interestingly, the section doesn't make reference to IBM's new, hosted, software management tool ESMT. The Enterprise Software Management Tool is described as an enhancement over the functionality currently provided by PA Online, providing "a full software inventory which details the number of licenses currently deployed and the number of licenses available to deploy. This can be updated in real-time to reflect any changes in requirement, meaning you always have a contemporaneous view of your IBM license position". What's not clear is how the tool will actually operate in order to provide the view of "how many licenses have been used, where and by whom". This seems to imply some degree of discovery across the client landscape - on an ongoing real-time basis - which would come with its own complexities and certainly, concerns. We'd be keen to hear from anyone who has or is looking to adopt this approach - please comment below or get in touch! What's not raised cynical eyebrows though is IBM's view of the benefits of being in compliance:
... we can all agree on that! So set aside some reading time and work your way through the site - it will be a valuable use of time, and ensure you bookmark it as you'll no doubt have cause to return on numerous occasions!
The Software Freedom Conservancy sues Vizio, Inc. for alleged violations of the GNU GPL covering software incorporated into certain Vizio smart TVs.
An early and widely publicised example of the impacts of such non-compliance was the 2008 lawsuit initiated by the Free Software Foundation (FSF) against Cisco Systems that alleged several of Cisco's consumer network routers used GPL licensed code. The litigation was settled with Cisco releasing the source code, making a contribution to the FSF, and appointing a compliance officer. Quite the kicker. In this latest action SFC asserts that all consumers of copyleft code deserve the opportunity to know, access and modify the code on their devices and is seeking the release of the complete, corresponding source (CCS) for all GPL’d components on Vizio TVs. The benefit? Well much as it was with the older analogue hardware TV's that would be repaired by technicians, coders would have the option to repair the software when the supplier potentially stops support for their older models (surely not from 'built-in obsolescence'?) And lets not forget the ethics involved given the FOSS history and the principles that underpin it. From its fruition in the 1990s and early 2000s when Linux and other GPL’d software was considered nothing more than experimental. From those curious beginnings grew the community of enthusiastic developers whose software has benefited and furthered the rights and freedoms of individual users, consumers, and developers around the globe. It is a culture worth preserving and that means keeping organisations who benefit from that culture honest. (SFC refers to this as 'Ethical Technology' meaning technology that serves its users rather than the corporations who profit from it and preserves and promotes the rights of those impacted by it). So if you are an organisation using open-source software, and in particular, incorporating it in proprietary commercial products, make sure you understand your compliance obligations with the relevant open source licenses. If you don't, you might soon find that letter arrives requiring you to release all of the IP you've built on top of the most excellent Free and Open Source Software that we all benefit from. The Software Freedom Conservancy is a 501(c)(3) nonprofit organization that is supported largely by individuals who care about technology and advocates for software that has been designed to be shared (using copyright licensing that allows users to freely use and repair it, and, in particular, forms of software licensing that use the restrictions of copyright to promote sharing called “copyleft”, such as the GPL).
In the absence of strict procurement practices and robust record keeping its all to common to see organisations struggling to retrieve their records of purchase backing-up their claim to entitlements. In fact how often do we hear "yeah we've got 20 licenses for that - they're listed on Dave's spreadsheet". Now lets be clear - the fact that it's on Dave's, or Susan's or anyone's spreadsheet does not constitute evidential fact. For that, you'll need the Proof of Entitlement if issued by the vendor, or the (signed) Contract containing the license grant, or the Order issued under it for the products in question. At a minimum if those are lost in the tracks of time (no doubt residing only in someone's email who has long departed the employ of the company), you'll need the latest invoice that shows the products and quantities that were covered by the last payment (ie. either actual purchase or renewal). Again, its all too common that it's not until an audit that organisations are forced to scramble through the purchasing, legal, IT et al records looking for some artefact to substantiate the otherwise baseless right of use claim for the vast overage of licenses that have been deployed! This trek down memory lane can be the most time consuming - and often fruitless - use of specialized resources, the cost of which is not generally recognized by management and similarly overlooked in the justification of a dedicated SAM function. So what's the alternative? Quite simply a process that ensures those essential records are properly recorded in an organized and readily accessible system, and are kept current through routine and ongoing ownership - once established this is not as much of an overhead as it might seem, and having all of that data at hand when challenged by a vendor can go a long way in underlining your disciplined approach and credibility in such a way that you'll be last on the next audit round list, if in fact on their radar at all. Now this will no doubt rally those skeptics with their "wait - I just call my reseller and say give me a list of what we own" approach, and while this might offer some solace it doesn't necessarily constitute proof in the same way that last document of fact - the invoice - does. How's that? Well for one example think of step-up licenses that will be printed there for all to see, but what about the original license it is based on (and worse, what if that original license is actually still in use!), or those 'from-SA' uplifts that require unravelling potentially years of purchase history to properly determine entitlement. All best avoided by having a routine practice supported by a specialized system in the first place ...
In this series we'll cover the foundations of SAM, and what they mean.Data is the essence of SAM, much as it is with most of technology. It's all there, somewhere, amassed over time, stashed away in the recesses of the organisation. It may exist (hopefully) in electronic form, or (lamentably) physical records filed and stored, most typically both. So we know the data's out there, the question is how - and where - do we start? The first step is to determine what data sources you can tap into, from the raw systems themselves through other collection platforms you might run such as CrowdStrike, Microsofts SCCM, IBM's ILMT, HCL's Bigix Inventory etc. With larger organisations the issue is always completeness - be it running agents or agentless via remote extracts - how do we know we're capturing everything we should ... and that can be a much more difficult proposition than it seems. The approach is to source as much data as possible and compare it, merge it, blend it, and massage it to get the best quality information you can - the issue today is not so much sourcing the data, its how to filter through it to find what's important, and to do that you'll need tooling. That means firstly figuring out what is most workable - and also most repeatable. This could be as simple as providing system logins to run application specific extracts, or remote connectivity as a centralised administrator, or even integrated access via API's. All act as feeds to your SAM system that will then do the hard data crunching and reporting work for you (for which ComplianceWare's pandas driven analytics engine is purposely designed). So that covers the inventory side of things - collecting the deployment information and associated identifiers (ie. the editions, statistics, capacities etc) necessary to derive your consumption levels, but then you'll need the associated Contracts and Licensing material as well to compare to your entitlements and establish your compliance position, and that's where things can get tricky. Most organisations - even those that are largely centralised - have some degree of local procurement (all the way down to problematic credit-card purchases) that make it difficult to collate the full and complete record of ownership. So you'll need to start with what is known, match that to the inventory you have identified exposing the shortfalls and gaps, and go looking for those great unknowns. This can be a long and even fruitless exercise at times, sometimes reliant purely on the knowledge of individuals (if they're still with the organisation that is), extending from business to technology teams, from legal to procurement, all depending on how controlled and robust the procurement processes are. The key here is to capture that information so its recorded and available from there on, and the whole exercise doesn't have to be repeated (as it would in the case of audits). Ideally your SAM system then allows you to maintain that connection of inventory to entitlements, organised by the contracts they were acquired (and operate) under. Any compliance issues can then be dealt with in a managed and controlled way, along with the potential benefit of savings from license consolidation, decommissioning, harvesting, or reuse, but we'll cover that in Series (#2). And the kick - data collection isn't a one-off, its an ongoing process that should be repeated as often as necessary based on the frequency and fluidity of change in your environment. On the plus side, once you have established the process it becomes much easier and efficient to rerun, and depending on your SAM system gain more intelligence each time (for example, ComplianceWare can compare different data captures and report the differences so that you can quickly identify what's changed, and what might need attention). Key takeaways then are:
Keep in touch for the upcoming SAM Foundation Series (#2) - Compliance Reporting.Vendor results can be a telling indicator of what might lie aheadWe regularly connect with the ITAM Review as a reliable source of information in the software domain and of interest this month is a comprehensive report from Rich Gibbons on the financial performance of some key software vendors - from the $5.6B loss of Google Cloud to the 29% rise in operating income (Q2) of Microsoft. In summary ...
Some marked differences in performance - particularly in the cloud space, with a watch and ready advice for some of the poorer performers - we all know where they head when times are tight ...
All might not be as it seems - check this list of ILMT gotcha's
Here are out top five tips for trimming your PVU sub-capacity report counts: 1. Incomplete Vitualisation - the 'TVM' predicamentIf your ILMT configuration is not fully or properly implemented you're likely to find incomplete virtualisation heirarchies in your VM Manager connections, which result in every affected VM being treated as a stand-alone physical machine at the highest PVU rating of 120 PVUs per core). This can quickly add up where you might otherwise be entitled to the likes of 70 PVUs per core. 2. Missing Software ClassificationsCentral to the accuracy of ILMT reporting is the much dreaded 'Software Classification' process. If you choose to ignore this painstaking requirement you can be sure you'll pay the price either in real terms or in time-draining dispute at your next audit. Essentially, every exempt PVU count in your environment needs to be catagorised as such, meaning instances that are to be excluded from PVU counts (which depending on the License Terms are likely Developer, DR, or Test installs) need to be individually identified as such via this (ongoing) activity. 3. Unrecognised BundlingAs a follow-on to the Software Classification issue above, you'll then likely notice that where you have installed Supporting Programs on a different server - where entitled to do so under the License Terms - the program will magically form part of the PVU count, ie. bundling is not recognised across servers. So once again you'll need to identify these instances and exclude them from the relevant count, making sure you add comments to qualify the classification. 4. Reallocation High-Water MarksSo you dutifully maintain your vCPU's to your level of entitlement, which, as you're permitted to do, includes the occasional reallocation across servers to match processing and performance needs. Given you've balanced the core counts out all is good - right? Well ... no, ILMT will track the high-water mark for each server in the 90-day reporting period, so for example a taking a core from a 4 vCPU server to assign to a 3 vCPU server will see both reporting as 4 vCPU servers for that period. To be in a position to challenge this make sure you have or take - and keep - separate records that evidence the reassignment of cores to negate any double counting. 5. Ghost DecommissioningSimilar to the above, you might think that decommissioning one server to deploy another would be quite within your rights as long as you (as always) don't exceed your level of entitlements. Well ... no, the decommissioned server will also report within the same 90-day period as the new server - potentially a bigger problem than the issue with high-water marks. So again you'll need to either classify the server accordingly, or ensure you have the right artefacts to contest any double recognition, or both. ... a lot of overhead right?Yes.And that's where a secondary source of truth can prove essential ...The world is certainly a different place than it was just weeks ago. From what was a normal days work to stay-at-home advisories, self-isolation and lock-downs, business and workers face enormous challenges. In such adverse times it's not possible to predict what the landscape will look like in the months ahead, but with the unfortunate loss of jobs and closure of businesses all we can know is that it will be a dramatically different place. Those that can and do keep operating are an imperative for the economy, both now and through recovery, and whilst it would be reprehensible of vendors to audit companies when the corner is turned, there are those that inevitably will still do so. So while there is much to contemplate and deal with in just keeping your business running, a quick check on some basic principles could avert some later issues. Consider some of the most common licensing pitfalls with typical BCP scenario's: Working From HomeWorking from Home means mobility - if you are allocating laptops and notebooks be wary of installation or device based licenses, all of which might be overlooked with the rapid deployment of SOE's and new devices. There may even be restrictions on what category of device the software can be installed on, or even where physically it can be used (eg. designated offices or specific geographic locations). Where applicable, check you mobility rights cater for your intended use, and are current (eg. Microsoft SA Benefits). Remote access can be another minefield where in the rush to get staff connected controls that would normally be in place might get overlooked. While solutions like an F5 BIG-IP Edge Gateway provide user based licensing to their own resources via secure VPN, other storefront and virtualisation products such as Citrix Gateway with VDI if not properly administered can be at greater risk of exposing applications unintentionally - make sure your access controls eg. AD Groups etc) are aligned to your licensing, and any additions to those secure groups have corresponding entitlements. Invoking DRIf you are in the position of having to invoke your DR (or partial DR) things will undoubtedly be more complicated. License transfer rights, powering servers up, or moving capacity from cold to hot can easily lead to over use. Migrating (or worse, extending) production workload to DR will certainly have conditions and constraints that if over-looked will leave you visibly non-compliant at a later date via audit trails such as SCRT or license server logs. Keep appropriate records that will help to mitigate any action you needed to take, and make sure you enable/track license migration alongside any workload you move. While we'd like to think some leniency would be afforded through these difficult times, keeping a good handle on your compliance position just makes good business sense. So stay compliant, but mostly, stay well, and stay safe.
IBM Announces its new "Authorised SAM Provider" Offering (IASP)While it appears the disgruntled messaging from clients is finally starting to register with some major vendors, a recent announcement from IBM (outlined here by the ITAM Review) by no means makes it an all clear. We're all for any move to make software licensing compliance simpler, and the IASP program for some large IBM customers might just do that - although by invitation only and accomplished by engaging one of just four designated IBM partners:
OKAY, SO WHAT's THE OBJECTIVE?In a nutshell, to offer those select few an alternative to IBM's License Reviews by operating a managed service that brings SAM expertise, tools, and knowledge to organisations who are perhaps struggling with those skills themselves - which happens to be exactly what we at Software Compliance have been offering our valued clients since 2016! HOW ABOUT the APPROACH?Once invited, an organisation selects an authorised partner who will then - through a defined scope of paid work - follow the standard licensing compliance process to create a baseline (using ILMT), perform an initial reconciliation, resolve any issues, and implement an ongoing management and control program, all done under an IASP Agreement that must be executed with IBM (covering a term of up to 3 years). ... And THE Benefits?The major attraction is that any licensing shortfalls discovered in the initial baseline can be resolved at the customers entitled price without any back-dating of S&S - and - an apparent waiver of any sub-capacity issues (tbc). ... and we all know how problematic (ie. costly) issues in this space can be! On the surface perhaps an admirable new direction from IBM, but does it really differ to how customers operating under the likes of an Enterprise Services & Software Offering (ESSO) have been treated for the last 10+ years? We think not - baselines were created, shortfalls resolved (albeit perhaps not as transparently), regular reporting was mandatory, etc ... so the only difference seems to be that the customer is required to engage one of just four designated partners.
Contact Us ... (before your Vendors do)
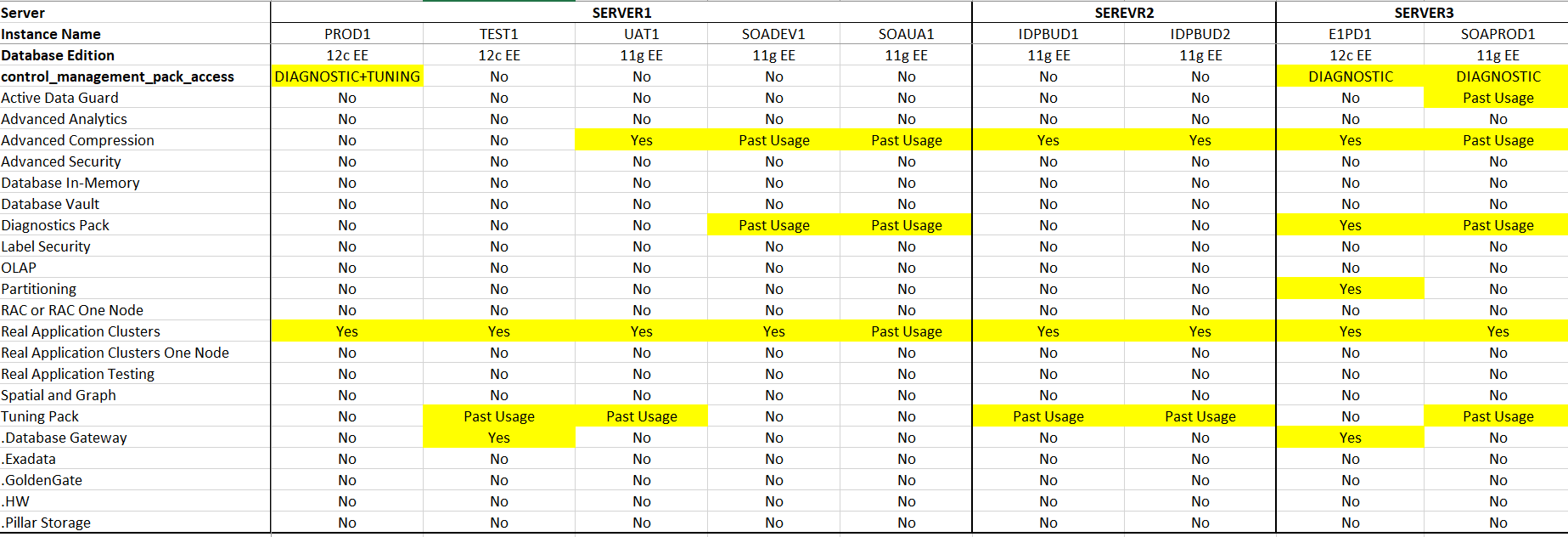
All might not be what You think - It's time to CheckSo all's fine with your Oracle Database - it's been installed for some time now, had a few upgrades, tweaks and tune-ups, you're across your NUP and Processor entitlements, so why have any concerns from a licensing perspective? Well, what about all of those Feature, Option, and Management Packs that lurk quietly in the background - have you checked on the status of those lately?
Worth checking to be certain before that next, friendly ... 'Oracle License Review'. To facilitate this Oracle provides a script - options_packs_usage_statistics.sql - which enables you to check Oracle Database feature usage, option usage, and management pack usage. The script lists, in two distinct sections:
The script can be run manually on an individual database or you can use Oracle Enterprise Manager Job System to automatically run the script on multiple databases, giving output like the below (with formatting added): Now with insight into the actual system settings a simple reconciliation to your licensing / entitlements will give you assurance that everything is in order, or alternatively highlight what needs to be resolved. A simple task well worth scheduling at least annually. and it's always good to keep a record for later comparison / compliance requirements (with ComplianceWare you can easily register the output as 'Verification' material alongside your licenses).
ADVERSE VIRTUALISATION TERMSCould You Be At Risk From Covert LICENSING TERMS?While some vendors are well known for their hostile terms towards specific forms of virtualisation (consider Oracle with VMware), others are not, slyly waiting for sufficient time to pass before issuing that dreaded ‘license review’ (aka audit) letter, hoping they can trap you with their archaic, antiquated, yet bizarrely enforceable terms that could see you severely punished if you have virtualised systems that fall under these conditions. Two current protagonists are coming to the fore in this space for their equally aggressive – and global – onslaught, hounding their loyal customers with totally unreasonable findings and outrageous demands for compensation. The problem emerged from the days of licensing physical installations by cores – easily managed when applications ran in their own dedicated servers, but with the shift to now omnipresent server farms, be it on-premise or cloud based, where their terms have not changed and don’t automatically recognise virtualisation as a means to limit the licensable metric (cores) you are at risk of paying for all of the physical cores in your entire Host estate. Consider the terms below extracted from the respective vendor agreements: Micro Focus End User License AgreemenT
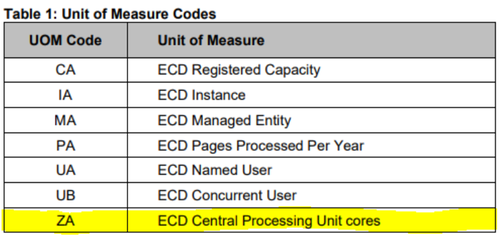
"Server License for CPUs. Licensed Software provided under this License Option gives Licensee the right to install the Licensed Software on a single machine or server ("Host Server"), or one or more Containers on the Host Server, and have the Licensed Software executed by up to the total number of CPUs, Cores, Integrated Facility for Linux processors ("IFLs"), Blades or other processing devices specified for the license in the applicable Product Order ("License Specification"). If the number of Cores is not specified for a CPU in the event a CPU is specified in the License Specification, such CPU shall be considered to be single-Core. A Server License for CPUs license covering all CPUs, Cores, IFLs, Blades and other processing devices that are contained in and/or can be accessed by the Host Server ("Total Processors") is required with all applicable license fees paid, even if one or more of such CPUs, Cores, IFLs, Blades or other processing devices are not accessing or running the Licensed Software. For example, if 32 Cores are the Total Processors on the Host Server, but only 16 Cores are utilized to execute the Licensed Software, a 32-Core Server License for CPUs license is required notwithstanding the fact that 16 of the 32 Cores may not actually be accessing the Licensed Software. Each Core on a multi-core CPU requires a Server License for CPUs license covering each such Core. For example a Host Server with Total Processors consisting of a single quad-core CPU will require a 4-Core Server License for CPUs license and payment of the license fees applicable to all 4 Cores." OPEN TEXT – ECD Central Processing Unit (“CPU”) ModeL Affected products are any of those on your Order From that have a UOM code of ‘ZA’: "Licensing and pricing is based upon the total number of CPU cores present in the computer upon which the ECD Software will operate. The ECD Software is licensed per physical dual-core device (“Dual-Core CPU”). Licensee must purchase an individual Software License for each Dual-Core CPU on which the ECD Software is executed or made available to execute." If you are in the unfortunate position of running any products that fall into the categories above, act fast. You will need to either move the affected applications to a right-sized physical box (with all of the accompanying issues that presents) or seek to agree with the vendor the appropriate virtualisation terms (and be wary – if they play this type of game that will likely just get their cash registers ringing). We find it hard to believe that such terms remain in vendor agreements, more so even deemed enforceable. If you've had the misfortune to have gone through such an affront, or think you might be about to, get in touch - we'd like to hear of (or help with) your experience.
IT SEEMS AUDIT SEASON HAS STARTED EARLY ...Revenue outlook must be a concern for a number of large, global corporates going by the number of audits we're aware of already this year - typically they seem to favour the mid to late part of the calendar. And lets face it, an audit is the last thing you need when you're just getting back to those major initiatives that need focus. Of course often its that very focus that leads to compliance issues - lacking the necessary oversight and controls in your IT landscape its not uncommon for BAU changes to cause a world of difficulty - a simple server refresh that introduces more cores, a change in access permissions that broadens the user base, or perhaps just plain old virtualisation. So what might target your organisation for attention by those loathed 'License Review Teams' waiting out there? Well the answer is, more than you might think. Typically something has got you to the top of the list. It can of course be within a common cycle such as at a contract renewal period, or an untimely prompt by one of those independent organisations whose entire income is through specialised and aggressive audits, but if not, what might cause it - and how might you prevent it? First, consider the common triggers:
If any of the above have you a little worried look for the most telling signal from your vendors of an impending audit - the unexpected communication that your "account team is going through some changes", which is simply a calculated, preemptive move to extricate any history and/or advocacy you might otherwise have had - prepare and get ready! all of those "but" arguments will get you nowhere - "but we had an agreement", "the account have known it was like this for years", "it was the licensing sold to us", etc etc. Alternatively, if you're feeling comfortable that you're not under any imminent threat its still a good idea to take stock and review your position against the common triggers. The best defense is without doubt a robust and competent software licensing function within your organisation that maintains the necessary level of control (and has the added benefit of warding off those vendors who would rather take on an easier, less capable target). When it comes to licensing and compliance its good practice to not treat your vendors like 'trusted partners' - keep in mind who they're actually working for, and who's paying their salaries. So - what to do:
Concerns? if you need any help, we're just a phone call away.
With a New Year ahead it's a good time to reflect on your IT Licensing status and Compliance Position - Are you confident that it's all under control?
Or does effective management of IT licensing just seem too vast and perhaps cost prohibitive to implement and maintain? It can seem that way - there are numerous and ever changing products, platforms, and models to complicate the situation, so how do you keep up? And what about the cost? - yes, Software Asset Management and Licensing Compliance to many executives can seem like an unnecessary spend, much like the early days of Disaster Recovery where the prevailing thinking was typically "why would we spend so much on hardware that's just going to sit idle?". Well compare that to the contemporary thinking today where Service Recovery is a given with any robust application - the spend is seen as a worthy investment, not just additional cost. At Software Compliance we recognised these factors as the perplexing problems the majority of organisations with broad IT solutions faced, and we decided to develop a solution that would work - and scale - to a vast array of companies, particularly SME's. So how did we do it? First and foremost we developed a tool to enable organisations to capture, contain and maintain that vast amount of software information important to them - their contracts, deployments, and licensing - the tool - ComplianceWare. Not only does ComplianceWare discover and track your software deployments, but it removes layers of licensing complexity by automatically tallying installations, performing product bundling where appropriate, and providing direct links to vendor licensing information to help you decipher whats relevant - all kept current for you by the team here at SWC. So if that solves the complexity issue, what about the next inhibitor - cost? Again, that was something we were very aware of. While there were existing solutions in the market they are typically high-end, bloated products aimed at large enterprises at a cost to match. We took a different approach - build a lean, cloud delivered, simplified application that organisations could subscribe to based on their requirements, and be there to provide ongoing support and expertise as those ever-changing products and platforms emerge and evolve. All at a such a compelling cost you'll wonder why you paid such exorbitant remediation fees in the first place (or perhaps might be about to!). So as holidays come to an end and we embark on another year it's a good time to reflect and ask yourself, in 2019 will we be:
It's not nearly as hard or as costlier a problem as you might believe it to be - find out more - get in touch and let's see how we might be able to help you gain more success in 2019.
As the chatter of audits increases around the industry the range of reaction can be outright fear to mild anxiety, but ... sometimes - enthusiasm! What I hear you say - Enthusiasm?? Well yes surprisingly - for those organisations who run a well informed and skilled software / licensing function - it offers the prospect of evaluating just how effective their investment in processes and tools has been, and make any adjustments as/if necessary. Similarly, it provides an opportunity for objective feedback to management in a discipline that is otherwise difficult to gauge - just think - how can you quantify ROI without having a relative measure to report against? The contrary position - where organisations have no certainty at all of their compliance state - is not a great place to be and certainly does warrant some anxiety. Not only is there the likelihood of remediation (at $$?? cost), but when you don't have a position what can you actually contest? There's no doubt that the 'arms-length' engagement of external auditors allows just that much more vendor independence to put more onus on you the customer - the audit will deliver a straight deployment report, leaving it to you to clarify what might be chargeable, and what might not. Examples .... development software that might be free, supporting products under one suite that might be dispersed across servers, or even bundles - permitted, but unless qualified by you will still be listed as chargeable installs. So it's worth considering just where you are on the compliance scale. Ask yourself these three key questions:
If you do - great! - check that the processes are running as expected and you can take any impending audit on without that gut-wrenching fear and anxiety. If you're lacking on any front though some attention is warranted. Start with ownership - who will be responsible and held accountable for your software assets? Then, how will you keep a current and complete record across it all? You'll no doubt arrive at the conclusion you'll need tools to help do it all efficiently and effectively, so the question becomes - which tool is right for you? What features and functions do I really need? What price do I then want to pay for it? The very questions that led us to develop ComplianceWare - our full featured, cloud-based product designed to meet the needs of organisations who don't want those top-end highly integration reliant, distended suites offered by some more well known global providers. ComplianceWare offers just those essential functions in an easy to use web-based application such as software discovery and deployment reporting, customisation via configurations and conventions, and of course a contracts and license repository. And by delivering just the essentials we can offer a price to match - that is, the most cost effective solution you will find in the market. Try it as a one-off managed service (perhaps even using that audit data you've just been asked to provide) and evaluate on your own estate, or as a term license have access when and as you need it. Take a look at the Documentation or request a Demonstration to find out more, and then we're always here to help you out as needed!
|
<
>
Archives
November 2023
|
|
Unravelling license complexity for Business
ACN 623 529 751 |
Privacy Policy | Terms of Use
|